“Like natural ecosystems, the cyber ecosystem comprises a variety of diverse participants – private firms, non-profits, governments, individuals, processes, and cyber devices (computers, software, and communication technologies) – that interact for multiple purposes”
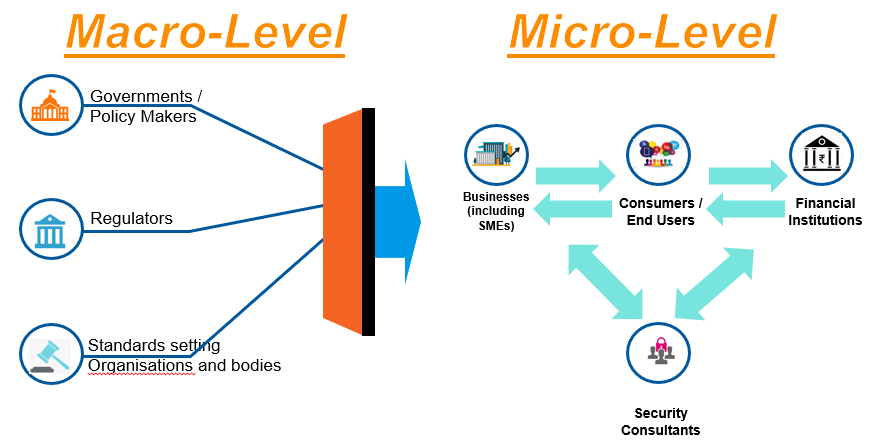
Ecosystem can broadly be divided into two categories
5 Steps towards a “Strategic Cyber Program”
1. Ensure that your cybersecurity strategy is aligned with business objectives and is strategically funded
2. Identify your most valuable information assets, and prioritize protection of this high-value data
3. Understand your adversaries, including their motives, resources, and methods of attack to help reduce the time from detect to respond
4. Assess cybersecurity of third parties and supply chain partners, and ensure they adhere to your security policies and practices
5. Collaborate with others to increase awareness of cybersecurity threats and response tactics
Pillars of Robust Cybersecurity Ecosystem
Cybersecurity is the practice of protecting computer systems, networks, and sensitive information from unauthorized access, theft, or damage. A robust cybersecurity ecosystem for any organization should be built on the following three strategic pillars:
1. Threat management and intelligence: This pillar involves identifying potential threats and vulnerabilities, and developing strategies to mitigate them. It includes monitoring networks and systems for suspicious activity, and implementing measures to prevent unauthorized access
2. Risk management: This pillar involves assessing the risks to an organization’s assets and developing strategies to mitigate them. It includes identifying critical assets, assessing the likelihood and impact of potential threats, and developing contingency plans to minimize the impact of a security breach
3. Security-centric culture and governance: This pillar involves creating a culture of security awareness within the organization. It includes training employees on security best practices, establishing policies and procedures for data protection, and ensuring compliance with relevant regulations
Cybersecurity ecosystem is a safety network that includes people, rules, tools, and devices all working together to protect our computers and online information. It aims to create a resilient infrastructure where all components work together in a harmonized way to identify, prevent, mitigate, and respond to all kinds of cyber threats
Other pillars of cybersecurity ecosystem are:
1. Integrity of Data in Its Original Form: This pillar ensures that data and information can be trusted, is accurate, and secure. It is the process of ensuring that data is accurate, secure, and unchanged during its entire life cycle
2. Availability For Authorized Parties: This pillar ensures that authorized users may easily access the data at any time and with ease. Possessing resources that enable convenient access to information is vital to maintain availability
3. Identity Authenticity: This pillar ensures that the identity of the user is verified and authenticated before granting access to sensitive information
4. Data Confidentiality: This pillar ensures that sensitive data is protected from unauthorized access and disclosure
5. Non-Repudiation: This pillar ensures that the authenticity and integrity of data is maintained throughout its life cycle, and that the data cannot be repudiated by the sender


















Comments