A robust cybersecurity ecosystem is essential to protecting sensitive data and preventing cyber-attacks. Here are some of the challenges that need to be addressed to ensure a robust cybersecurity ecosystem:
Shortage of skilled professionals: The demand for cybersecurity professionals is increasing, but there is a shortage of skilled people to meet this demand. This can put organisations at moderate to extreme risk for cyberattacks.
Remote and hybrid working: The COVID-19 pandemic has accelerated the digital transformation and made it clear to companies that they need to prioritise security. Remote and hybrid working arrangements have created new vulnerabilities that need to be addressed.
Security in the crypto ecosystem: Cryptocurrencies are becoming more popular, but they also present new security challenges. The decentralised nature of cryptocurrencies makes them difficult to regulate and secure
Ransomware attacks: Ransomware attacks are becoming increasingly sophisticated and are a growing threat to organisations. Cybercriminals are using ransomware-as-a-service models, which provide them with access to ransomware tools, infrastructure, and support services for a subscription fee.
AI-driven attacks: Artificial intelligence (AI) and machine learning are revolutionising cybersecurity, both as a new vector for attack and as powerful tools that enable organisations to defend against increasingly menacing cyber threats. Malicious actors are leveraging AI to launch more sophisticated attacks, while AI-driven data security solutions can be used to automate many of the tasks that are currently performed manually.

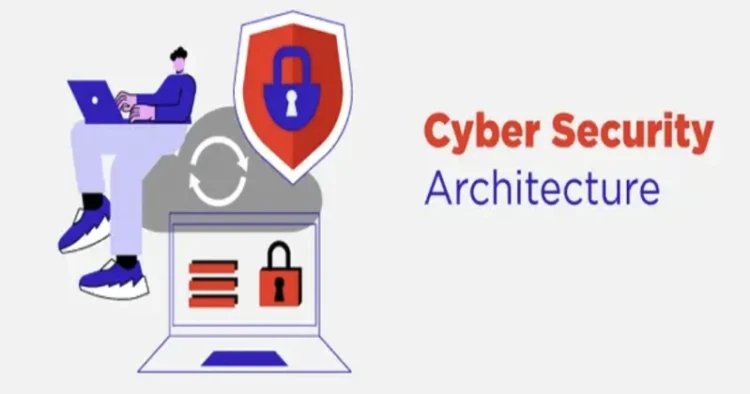
Architecture of a Robust Cyber Security System
A cybersecurity architecture is a comprehensive approach to designing and implementing security measures that protect an organization’s digital assets from cyber threats. It is a multifaceted strategy that includes security policy, risk management, and the determination of controls and procedures.
A robust cybersecurity system should have the following elements:
Network security architecture: This involves the systematic design and implementation of security measures to safeguard an organisation’s computer networks against unwanted access, cyberattacks, and data breaches. It entails the installation of firewalls, intrusion detection/prevention systems, and other network security controls to protect the integrity and confidentiality of data transmitted across the network.
Application security architecture: This involves the systematic design and integration of security measures into software applications to prevent vulnerabilities and illegal access. Secure coding practices, authentication systems, and encryption are used to ensure the confidentiality and integrity of sensitive data processed by apps.
Information security architecture: This involves the combination of security measures with business objectives across people, processes, and technology. It ensures that security measures are aligned with business objectives and that sensitive data is protected from unauthorised access.
A cybersecurity architecture framework specifies the structure, standards, policies, and functional behavior of a computer network, including both security measures and network features. It is designed to reduce risk, ensure compliance, and effectively address security issues in software development.
Cyber Security Policies
Cybersecurity policies are a set of standardised practices and procedures designed to protect an organization’s network from cyberattacks. These policies detail the practices, standards for behaviour, and measurable goals that an organisation requires to prevent and recover from cyberattacks.
A cybersecurity policy is a useful tool for educating staff members about the significance of security. It details each employee’s obligations to safeguard the organisation’s systems and data.
Here are some examples of cybersecurity policies that an organization might have:
Acceptable Use of Data Systems Policy: This policy stipulates the suitable use of computer devices at the corporate/company. These rules protect the authorised user and the company as well. Inappropriate use exposes the corporate to risks including virus attacks, compromise of network systems and services, and legal issues.
Account Management Policy: This policy determines a standard for the creation, administration, use, and removal of accounts that facilitate access to information and technology resources at the corporate.
Anti-Virus Policy: This policy was established to assist in preventing attacks on corporate computers, networks, and technology systems from malware and other malicious code.











![A Representative image [ANI Photo]](https://organiser.org/wp-content/uploads/2025/12/representative-image-e1765612818961-120x70.webp)







Comments