Prafulla Ketkar
The Centre has come up with the National Cyber Security Policy, 2013 (NCSP) for securing computing environment and facilitating regulatory compliance. Besides the revelations on the electronic surveillance and data-mining programme by the US National Security Agency, possible loss of data to Chinese hackers in the eastern command headquarters of Navy at Vishakhapattanam and breach of the main National Informatics Centre email server, which serves all government departments, necessitated this policy formulation. The fourteen point objectives enshrined in the ambitious document envisage 24×7 National Critical Information Infrastructure Protection Centre (NCIIPC), public-private partnership in information security and creation of a robust workforce of five lakh cyber security professionals in five years. Though the objectives are noteworthy, the operational aspects are missing in the policy document.
The problem with cyber space management lies in tackling individual cases, the intruders may not be operating from the land where laws exist and laws may not be applicable from where intruders operate. In case of national security issues, the deliberate use of private players by foreign governments makes the issue more complex. More importantly, the dual objective of data privacy and collection of threat information is an oxymoron. In this context, the operational and coordination aspects of various agencies are pertinent. What will be the role of security agencies in the operationalisation process, how and to which extent private players be used, what will be the blueprint for creation of cyber warriors and how can indigenous technologies be developed to ensure cyber security are some of the critical questions requiring an answer.
Since the introduction of Information Technology Act, 2000 and subsequent amendments in it, there is hardly any improvement in the situation on cyber security. The private agencies, hand in glove with their foreign masters, will hardly be of any use in this regard. Police machinery in India is ill-equipped in dealing with the cyber issues. They have to be technically trained, otherwise solution will be more disastrous than the problem.
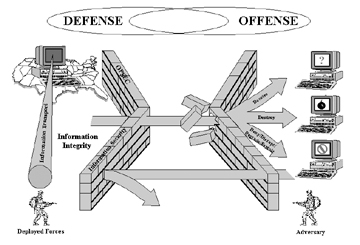
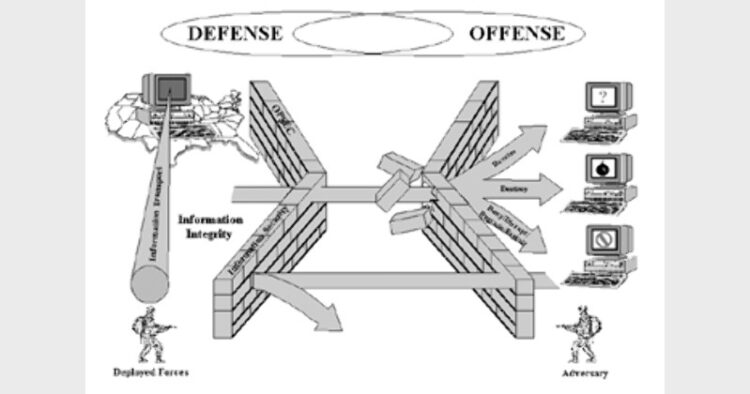
Until now, revolution in Information Technology has been viewed only as a technological and/or economic issue in India. In the age of Information Warfare (IW), cyber security policy should include actions taken to achieve information superiority by affecting adversary’s information, information-based processes, information systems and computer-based networks, while defending one’s own information, information-based processes, information systems, and computer-based networks. Therefore, mere defensive mechanism of data protection would not suffice but integrated strategy along with offensive machinery need to be incorporated in the National Cyber Security Policy.












Comments