Cybersecurity is a rapidly evolving field, and its history is a fascinating one. The first recorded cyber-attack dates back to the 1970s, when a researcher named Bob Thomas created a program called Creeper that could move between computers on ARPANET, a precursor to the internet. Since then, the field has grown and evolved to keep pace with the ever-changing threat landscape.
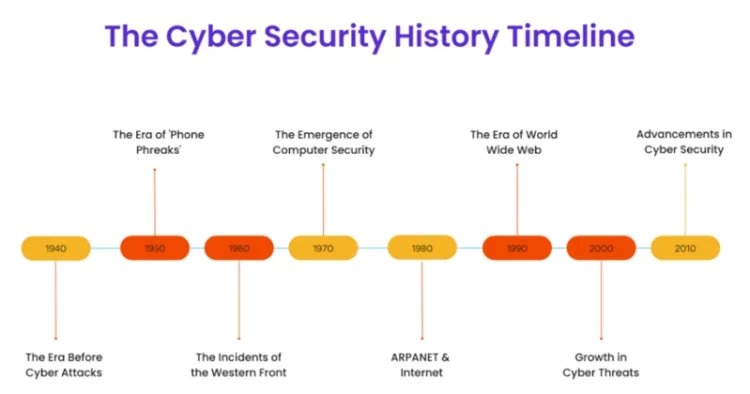
Here’s a brief timeline of some of the key events in the history of cybersecurity
- 1940s: The first digital computer was built in 1943, but cyberattacks were challenging to execute for about 20 years after that because only a few people had access to the enormous electronic machines, which weren’t networked and only a few people knew how to operate them.
- 1970s: The first recorded cyber-attack occurred in the 1970s, when a researcher named Bob Thomas created a program called Creeper that could move between computers on ARPANET, a precursor to the internet.
- 1980s: The first computer virus was created in the 1980s, and the first antivirus software was developed in response.
- 1990s: The World Wide Web was invented in the early 1990s, and with it came new security threats such as phishing and malware.
- 2000s: The 2000s saw a rise in cyber espionage and cyber terrorism, as well as the development of new security technologies such as firewalls and intrusion detection systems.
- 2010s: The 2010s saw a significant increase in the number and severity of cyber-attacks, including high-profile breaches of major corporations and government agencies.
- 2020s: The current decade has seen a continued increase in cyber-attacks, as well as the emergence of new technologies such as artificial intelligence and the Internet of Things, which present new security challenges.
Artificial Intelligence in the field of Cyber Security
Artificial Intelligence (AI) is another technology that has started impacting government departments and internal organisations in a major way. Artificial Intelligence applications are based on neural networks, machine learning, deep learning and Natural Language Processing algorithms. Machines act like humans only after they are trained well to accomplish specific activities by processing huge amounts of data and identifying patterns in it. The growing interest and value proposition of the technology is resulting in IT companies/software vendors to include Artificial Intelligence in most of their service propositions. Major initiatives in the field of Artificial Intelligence have been taken by Google, Apple, Amazon and others. Government of India has appreciated the immense potential of Artificial Intelligence and has made significant investments to use it for better governance and service delivery. Artificial Intelligence has the potential to make cybersecurity more efficient and responsive against ever increasing threats and improve the cyber security posture of an organisation.
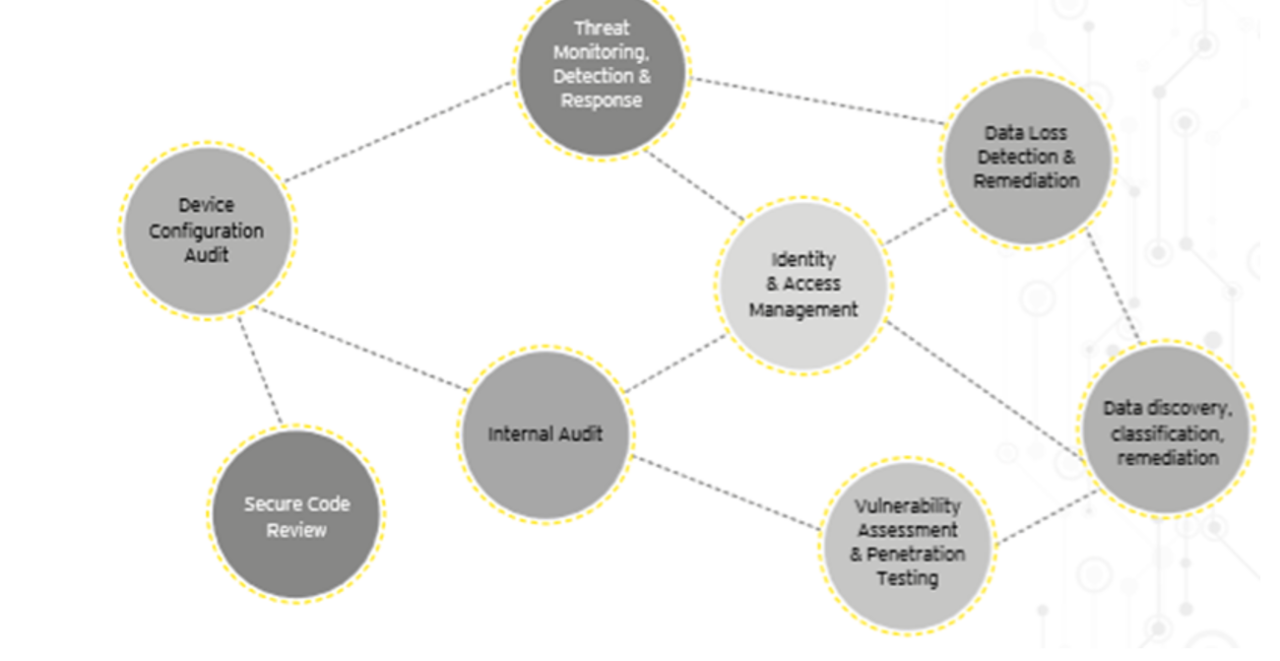
Threat monitoring, detection and response: Artificial Intelligence and Machine Learning (ML) allow the systems to monitor a wider range of evolving threat vectors (rather than monitoring threats against previously identified signatures). Machine learning can track anomalous behavior easily and help in predictive analysis of threats and attacks. Complex analytics using historical data combined with clustering, clipping, data visualisation etc. can be carried out without human intervention and allow security administrators to respond in near real time to security events and incidents. This will take threat detection and alert generation to the next level.
Secure code review: NLP techniques (Natural Language Processing algorithms) are utilised in automated code review for better detection and reporting of bad coding practices or security vulnerabilities. Automating code reviews can help reduce costs, ensure code health and increase productivity by focusing on the most harmful vulnerabilities.
Audit: Machine Learning can increase efficiency of configuration management, configuration audit and cyber security audits by removing human errors and biases. These solutions can enhance the performance and reduce the risk in internal audits by reviewing a larger data set as compared to evaluating a representative sample as done in conventional internal audits against known internal control red flags, thereby ensuring audit completeness and quality reports.
Access management and network monitoring: Access management is another area where Artificial Intelligence and Machine Learning can increase efficiency and effectiveness. Cyber security of systems, applications and data bases can be improved through continuous learning and updation of rules. They can also aid in monitoring network traffic and identifying any abnormal activity and raising alarms or taking pre-emptive actions to block any traffic which can harm the networks or applications, thereby integrating the functionalities provided by multiple security tools in a SOC.
Data discovery, classification and loss detection/prevention: Machine Learning techniques can be used to enhance offerings by typical Data Loss Prevention (DLP) solutions by automating classification, monitoring and prevention of sensitive data loss by using predictive models to identify sensitive personal or health or financial information and tracking access patterns to these data sets from new/unusual activity from existing sources.
Vulnerability assessment and penetration testing: Artificial Intelligence based vulnerability scanning applications are able to crawl dynamic pages, detect vulnerabilities which otherwise require human intelligence, thereby reducing cost and increasing efficiency and reducing false positives.
Blockchain Technology empowering Cyber Security
Blockchain is a distributed infrastructure technology – it is a decentralised ledger that keeps a record of each transaction that occurs across a network which enables a decentralised exchange of trusted data – a ‘shared record book. Blockchain, as a technology, focusses on integrity and immutability of transactions.
Blockchain promises to:
- Increase the speed, the efficiency and the security of transactions and ownership transfers of digital assets.
- Remove bottlenecks, a phenomenon associated with central servers.
- Eliminate the need for central authorities to certify ownership and clear transactions.
- Reduce fraud and corruption by providing a transparent public and auditable ledger.
- Reduce administrative cost using agreements that can automatically activate secure and trusted actions based on specific conditions (smart contracts).
Blockchain will enable a wider variety of transactions, such as collecting taxes, delivering benefits, issuing documents and recording properties. Governments can use blockchain in sectors such as public safety, social services and identity management. A blockchain uses a decentralised distributed ledger system rather than relying on a single trusted central authority. With distributed ledger technology (DLT), transactions are recorded across every network node, so cybercriminals face challenges viewing, stealing, or modifying data. It is designed to create trust amongst participants in areas where trust is hard to come by.



















Comments